Digital banking fraud: Best practice for technology-based prevention
The shift of banking to digital channels is creating a revolution in banking fraud. Until a few years ago, this was the preserve of small-scale criminals attempting to steal relatively modest sums. But today, digital banking fraud is a major international industry in which sophisticated criminal groups employ increasingly sophisticated tools – and frequently collude with corrupt bank staff – to steal very large sums. This in turn has pushed up the liabilities that banks must absorb to cover the losses their customers suffer due to fraud.
As digital channels have multiplied, so have the routes that fraudsters can use. And their options are about to expand again with the implementation of Open Banking and the coming into effect of Europe’s second Payment Services Directive (PSD2). This will present a new set of challenges for banks, who will remain liable for losses caused by unauthorized transactions through these new digital channels.
Against that troubling background, we’ve complied a page that cover the what, why, and how of digital banking fraud. With this informative page, we hope to help banks anticipate the upcoming digital banking fraud threats, understand weaknesses, learn latest best practices so they can not only detect digital banking fraud, but also prevent it.
Use the table of contents below to navigate through the page:
- The context: fraud on an industrial scale
- What are the looming challenges of open banking?
- The risks: how and where cyber-fraud happens
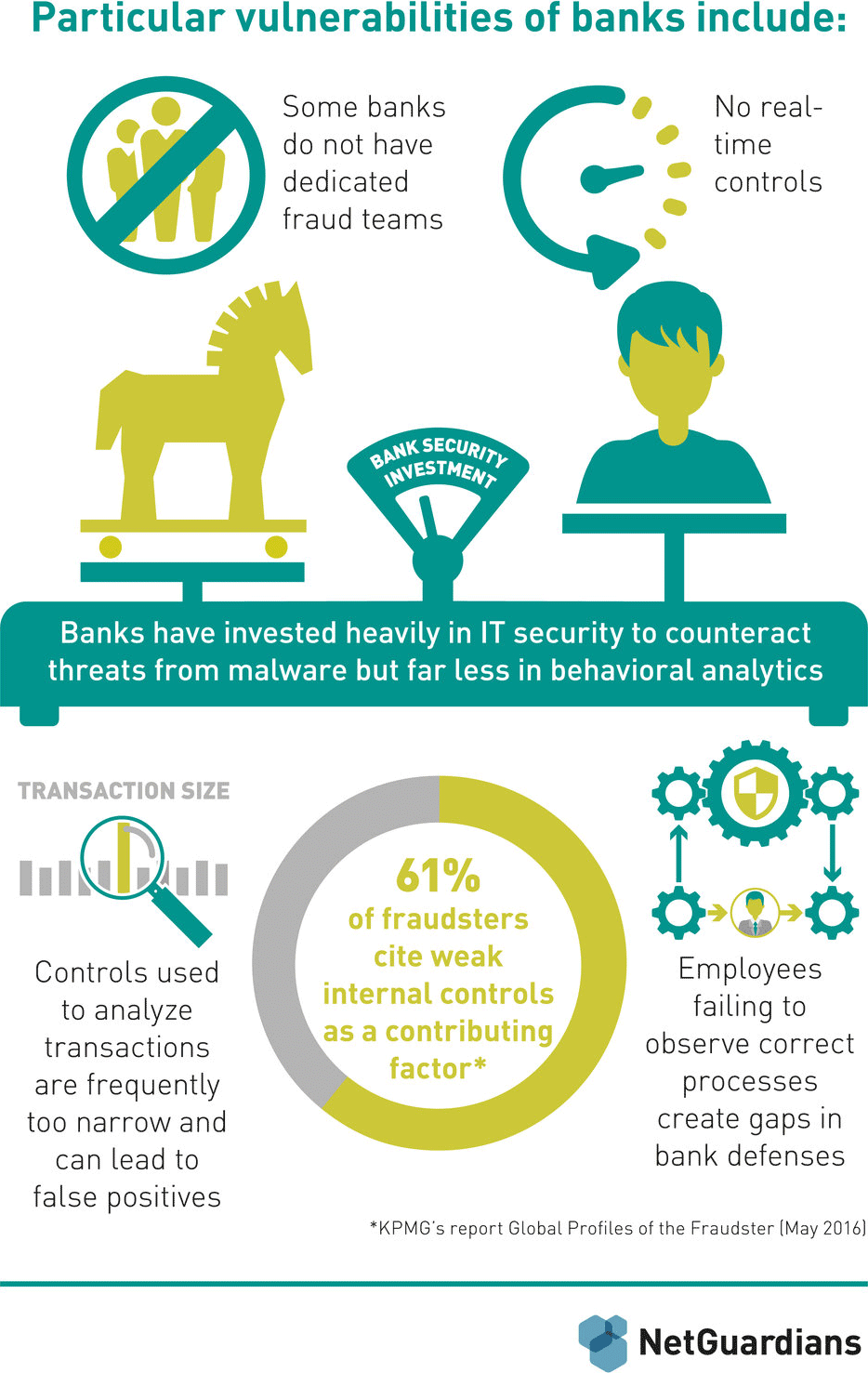
- Know your weaknesses: the three Cs – customers, controls and culture
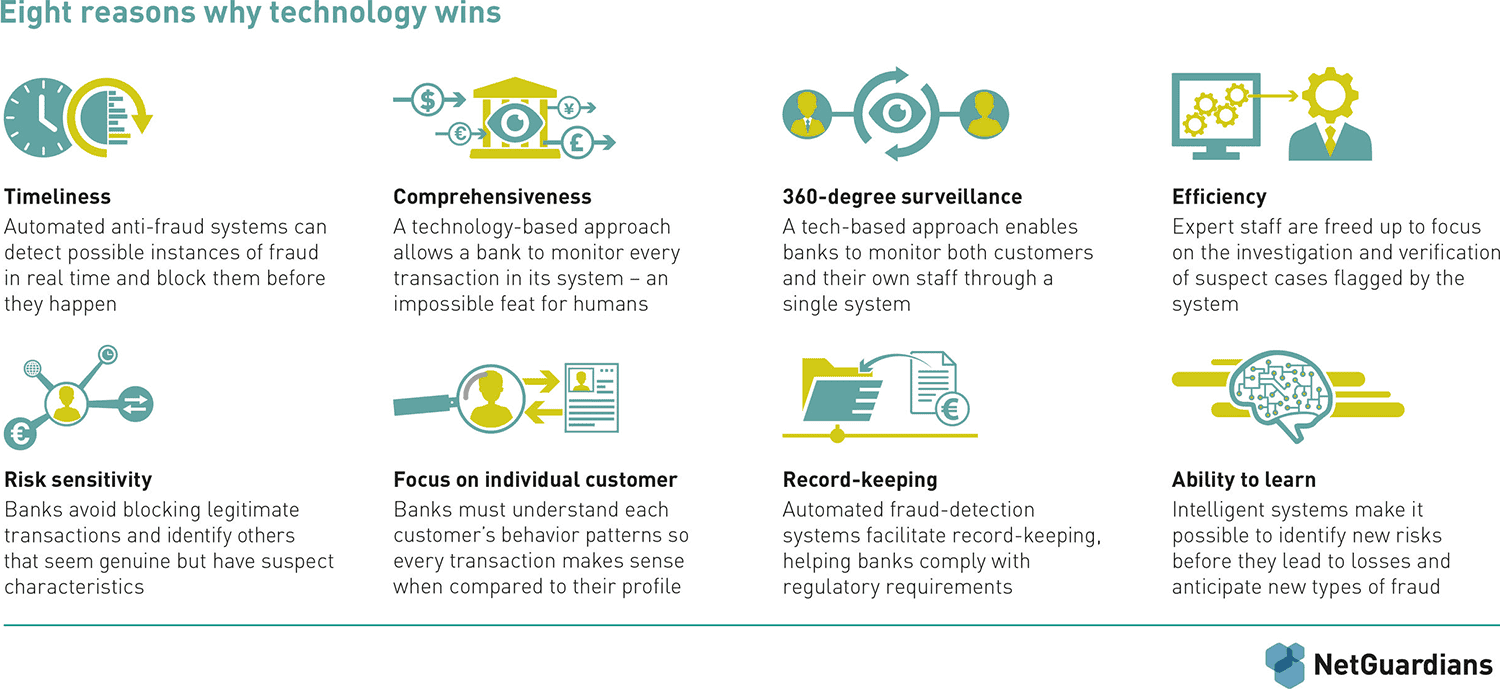
- The case for technology: eight reasons why it wins
- Outlines for a tech-led solution: behavioral data analytics holds the key
- Conclusion